Reverse Engineering Malware: Techniques And Tools For Analyzing And Dissecting Malicious Software
Cybercriminals commonly employ malicious programs to obtain unauthorized system access, exfiltrate sensitive information, or disrupt essential services. In order to defend against these threats, cybersecurity professionals use various approaches to analyze mechanisms of a malware’s operation and how best it can be prevented.
Reverse engineering malware is one such analysis technique that involves disassembling the program’s components and functions to gain insight into its behavior, structure, and capabilities. This process can assist cybersecurity professionals in recognizing the attack vector of a given threat, pinpointing its infection and propagation methods, as well as crafting effective countermeasures against it.
In this article, we explore in detail the various techniques and tools used in reverse engineering malware, and demonstrate their practical application through a real-world case study.
Why to Reverse Engineer Malware?
Reverse engineering malware can be particularly insightful for identifying zero-day vulnerabilities in software, which are otherwise unknown to respective software vendors and can be exploited by attackers to gain access to systems and data. Analyzing malware also enables reverse engineers to identify exploit code and the vulnerability it exploits – ultimately helping develop an invaluable resource that allows them to create patches or other mitigation strategies.
Reverse engineering malware can also be beneficial for mimicking the techniques attackers employ to avoid detection and propagate it. Although by employing obfuscation or anti-analysis techniques, malware developers make it harder to analyze their code, reverse engineering the malware can identify these tactics and create countermeasures designed to detect and prevent future outbreaks.
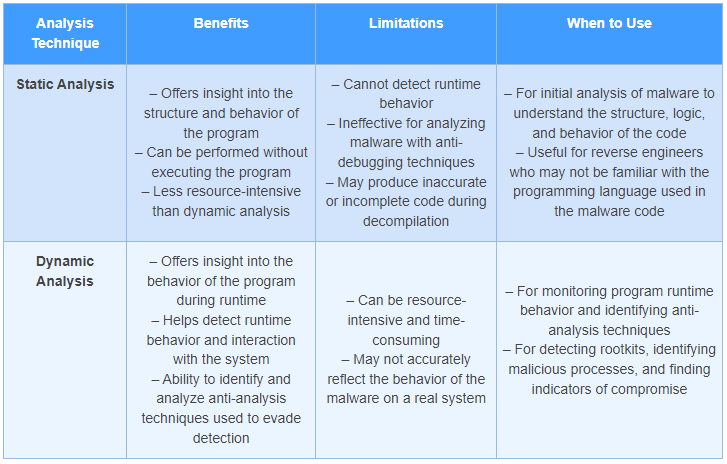
Techniques for Reverse Engineering Malware
The choice of analysis technique depends on the type of malware being analyzed and the information that needs to be gathered. While both static and dynamic analysis techniques have their benefits and limitations, leveraging a combination of both static and dynamic analysis techniques is often the most effective approach for analyzing malware.
Static Analysis
Static analysis is the practice of dissecting the binary code of a malware sample without actually running it. This technique helps in comprehending how the malware functions, its capabilities, and what kind of damage it may cause. There are three primary techniques used in static analysis:
1. Disassembly: This process transforms a program’s binary code into human-readable assembly code and enables reverse engineers to decipher the structure and flow of the code.
For example, if a reverse engineer comes across malware with an unknown payload, they can use disassemblers such as IDA Pro or Ghidra to examine its binary code and locate its entry point. Once identified, analysis of the assembly code can provide insight into how the payload behaves.
Disassembling tools can also be employed to identify malware packers, which use compression and obfuscation techniques to avoid detection. By disassembling the packed code with a disassembler, reverse engineers can decipher its functionality and create signatures for future detection.
2. Decompilation: This process converts the machine code of a program back into higher-level programming languages, such as C or C++ to make it simpler for reverse engineers to analyze the program’s logic and structure.
For instance, to reverse engineer malware samples written in obscure programming languages, analysts can utilize decompilers such as Hex-rays IDA Pro or Ghidra to convert the machine code into a more familiar programming language. Once this code has been converted to something familiar, analysis of its behavior becomes much simpler.
Decompilation tools can also be employed to detect malware obfuscation techniques, which make code more difficult to read and comprehend. By decompiling the code, reverse engineers are able to recognize these techniques and undo them in order to gain insight into its true functionality.
3. Symbolic Execution: This technique utilizes variables and symbolic values to simulate the execution of a program. Symbolic Execution can be helpful in understanding how malware code interacts with the system and changes its behavior.
For instance, if a reverse engineer comes across malware that employs anti-debugging techniques, they can use symbolic execution to execute the code and circumvent these measures. After bypassing these safeguards, they can analyze the code’s behavior to uncover its functionality.
Symbolic execution tools can also be employed to detect zero-day vulnerabilities in software. By running a program symbolically, reverse engineers can identify inputs that cause certain code paths, leading to the discovery of vulnerabilities that could be exploited by attackers.
Dynamic Analysis
Dynamic analysis involves executing the malware sample in a controlled environment to observe its behavior. This technique is useful in understanding how the malware operates, what its capabilities are, and what kind of damage it can cause. There are three primary techniques used in dynamic analysis:
1. Debugging and Tracing: These techniques are useful for recognizing a malware’s control flow, detecting anti-analysis techniques used to avoid detection, and comprehending how the malware interacts with the system during run time.
For instance, when a reverse engineer comes across malware samples communicating with remote servers, they can use debuggers such as OllyDbg to attach to the running process and analyze its behavior. By setting breakpoints on network-related functions, the reverse engineer can intercept traffic between them and analyze its content. Once collected data has been analyzed, they can deduce which communication protocol was utilized between malware and its server.
Tracing tools such as Sysinternals Process Monitor can also be employed to track system activity associated with malware. A reverse engineer can use such Process Monitors to monitor registry and file system access, along with network activity, in order to detect any changes made by the malware and gain insight into its behavior.
2. Memory Forensics: This is the process of studying contents of a computer’s memory using memory analysis tools and extracting information of running processes or memory dumps. Memory analysis tools are typically used for gaining insights into the computer system’s current state and can additionally be employed to detect malicious processes and rootkits.
For instance, if a reverse engineer believes that malware has injected code into an official process, they can use memory analysis software such as Volatility to identify the code and assess its functionality. With this approach, they also have access to processes and DLLs loaded in memory, plus network-related data stored there. Instances where a reverse engineer believes there has been an installation of a rootkit on their system, they can use Rekall memory analysis software to detect any suspicious processes or modules loaded in memory.
3. Emulation and Sandboxing: These are powerful techniques that enable malware to be executed within a supervised environment and observed for its behavior. When used together, these processes collectively help us comprehend how malware operates, what harm it can cause, and how best to defend against it.
For instance, if a reverse engineer comes across a malware sample that installs a rootkit on a system, they can use an environment such as Cuckoo Sandbox to execute it and analyze its behavior. This provides a controlled setting where malicious code can be executed without impacting the host system. Once understood, researchers can devise strategies to remove rootkits from infected machines.Emulators such as QEMU can also be utilized to simulate different operating systems and test malware samples on them. Doing this gives us valuable insights into how malware operates and the type of harm it may cause.
Technical Walkthrough: Reverse Engineering Malware in a Real-World Scenario
Consider a scenario in which a security analyst has identified a suspicious executable file on a Windows system that appears to be communicating with a remote server. The analyst suspects that the file is a Trojan malware and wants to analyze it to determine its behavior and steps to remove it from the system.
Possible Steps
Obtain the executable file: The first step is to obtain a copy of the suspicious executable file from the Windows system for analysis.
Perform static analysis: Use a disassembler, such as IDA Pro or Ghidra, to perform static analysis on the executable file. This can include disassembling the code to understand the program’s structure and behavior, and identifying any obfuscation techniques used by the malware to evade detection.
Perform dynamic analysis: The analyst should also use a debugger, such as OllyDbg or x64dbg, to perform dynamic analysis on the malware. This can include debugging and tracing the code to identify how the malware interacts with the system and any anti-debugging techniques it may be using.
Monitor network traffic: Use a network analyzer, such as Wireshark or tcpdump, to monitor the network traffic generated by the malware. This can include identifying the IP address of the remote server the malware is communicating with, and the types of data being sent and received.
Identify malware functionality: Based on the information gathered from static and dynamic analysis, the next step is to identify the malware’s functionality, such as analyzing the amount of damage it can cause, how it communicates with the command-and-control server, and whether it uses any rootkit or anti-detection techniques.
Develop a remediation plan: Post-analysis, develop a remediation plan to remove the malware from the infected system and prevent it from spreading to other systems. This can include updating antivirus software, patching vulnerabilities exploited by the malware, and educating end-users on how to avoid malware infections in the future.
Final Thoughts
Reverse engineering malware is a complex and challenging task that requires technical expertise and the use of specialized tools. In this article, we explored how static and dynamic analysis techniques suit different use cases, and a common approach to gain valuable insights into the behavior of malware is to use both the techniques together.
Besides choosing the analysis technique and tools, here are some additional points to note before you reverse engineer malware:
Ensure that you have the appropriate technical expertise before attempting to analyze malware
Conduct malware analysis in a secure and isolated environment that is not connected to any production systems
Use multiple techniques to get a complete picture of the malware’s behavior and functionality
Stay up-to-date with the constantly evolving tools and techniques for malware analysis and defense
Keep detailed notes and documentation of the analysis process for information sharing and replicating the analysis
While it is difficult to predict the future of cybersecurity, it is unlikely that we will ever completely eliminate the threat of malware. As technology continues to advance, cybercriminals will continue to find new ways to exploit vulnerabilities and gain unauthorized access to systems and data.
Ultimately, a world without malware may not be entirely possible, but by taking proactive measures to improve our security posture, we can significantly reduce the risk and impact of malware attacks, and make the digital world a safer and more secure place.
This article has already been published on javelynn.com/cloud/reverse-engineering-malw..